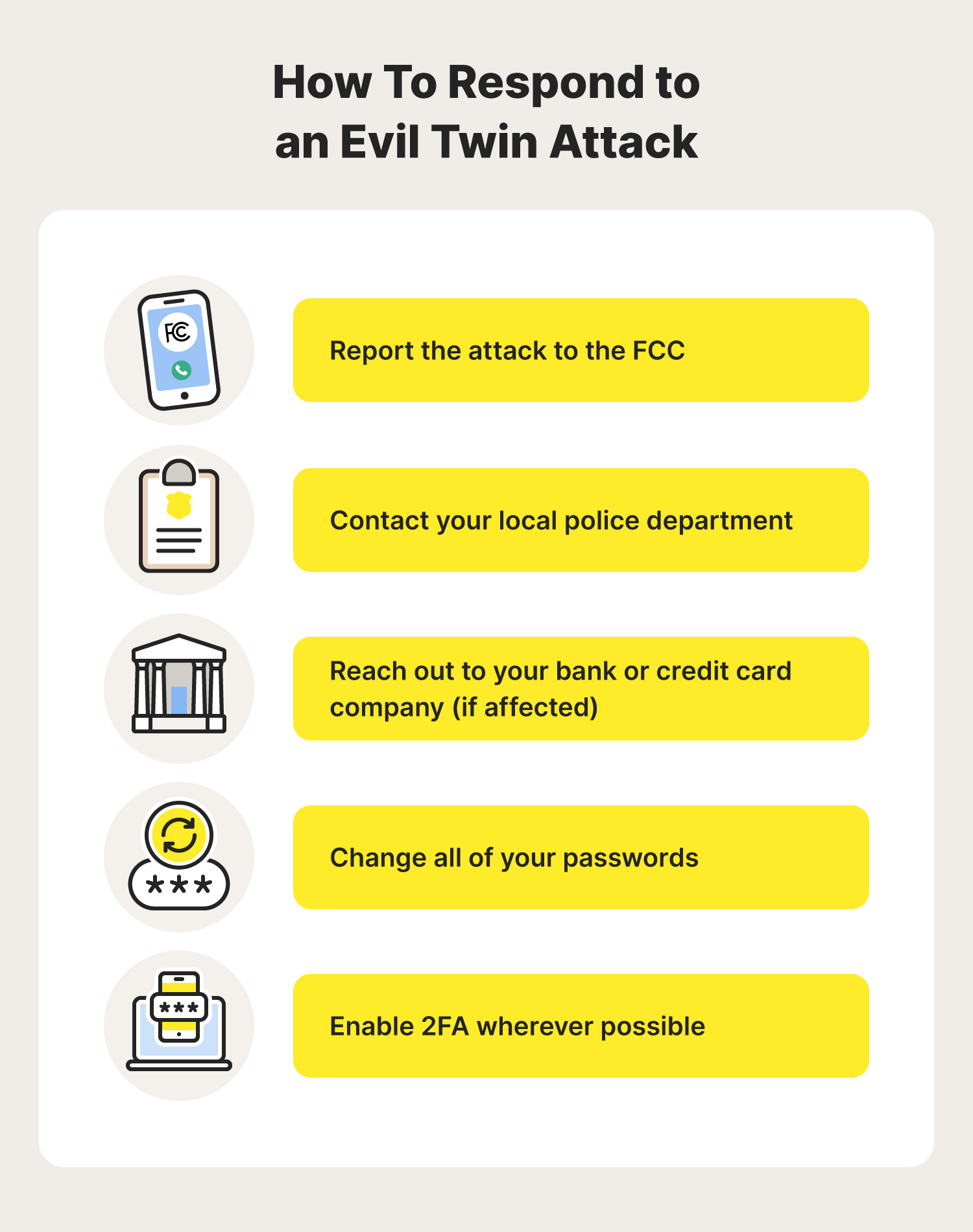
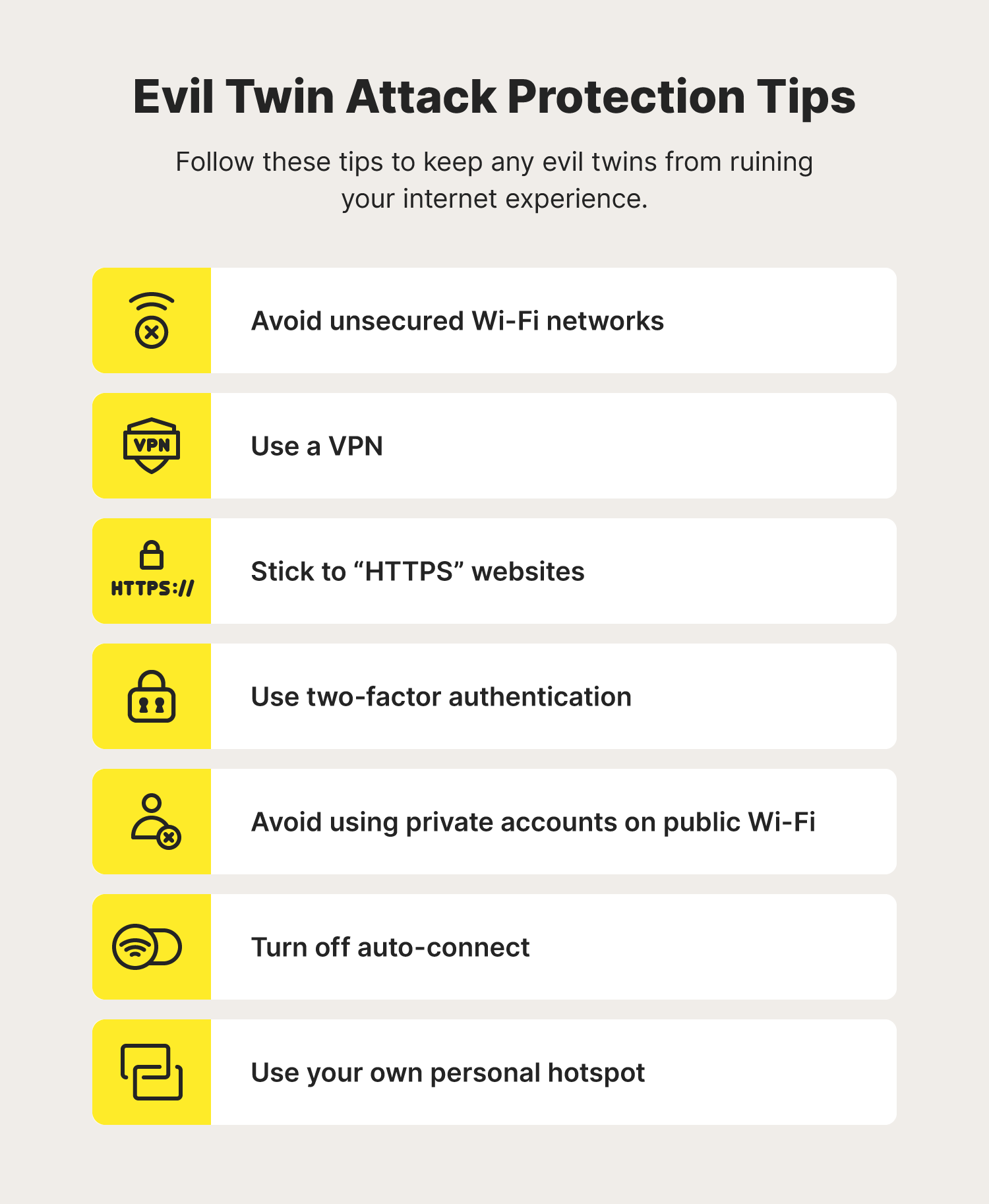
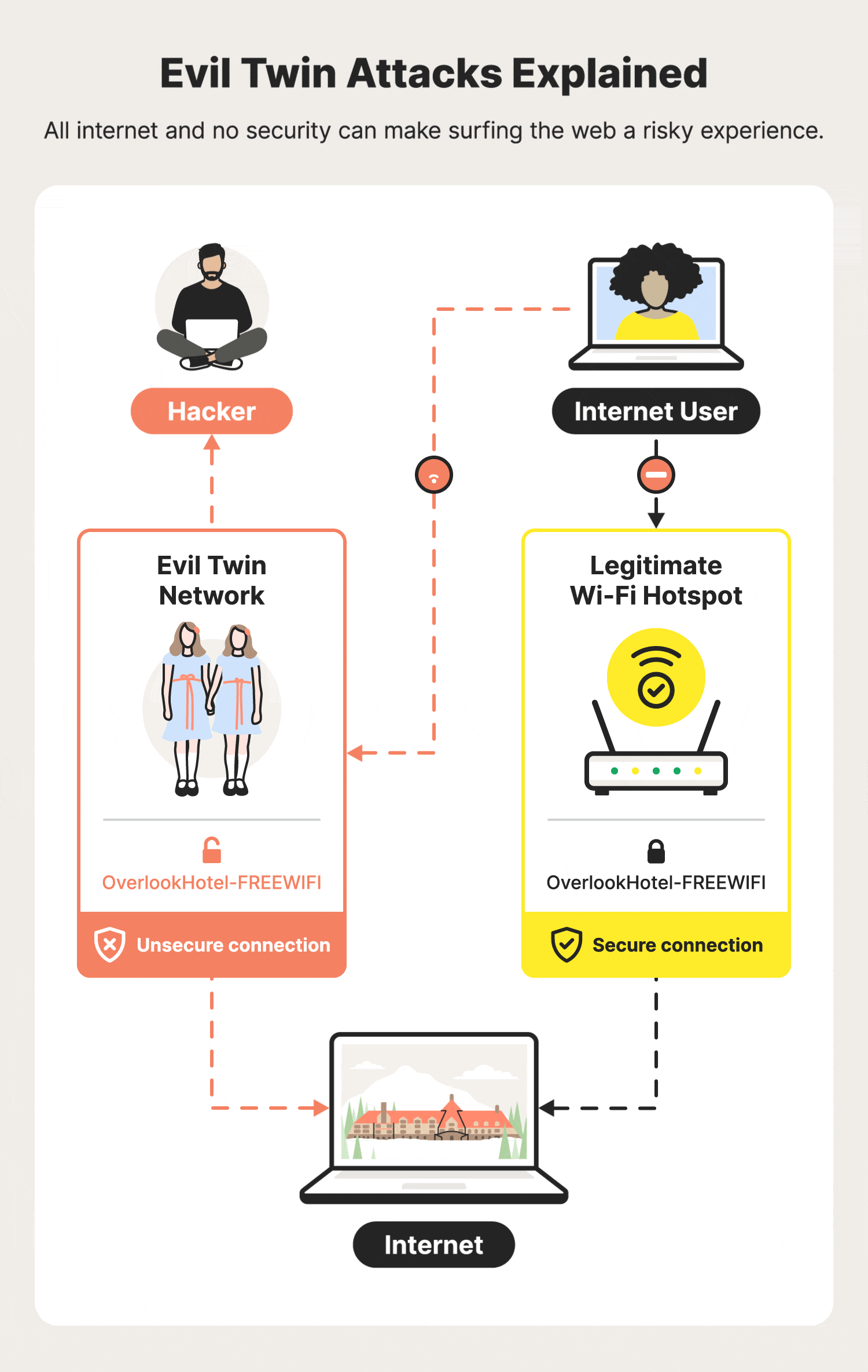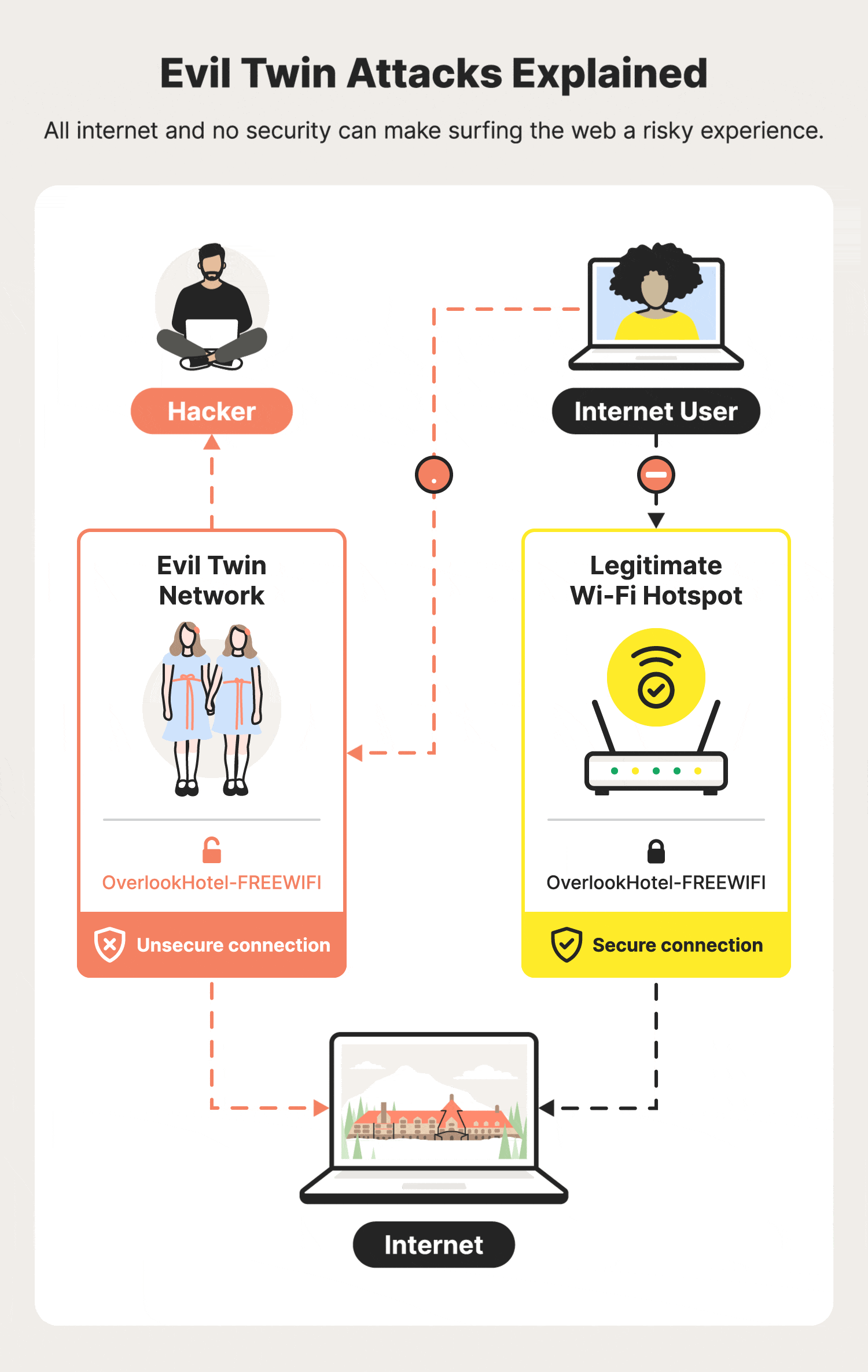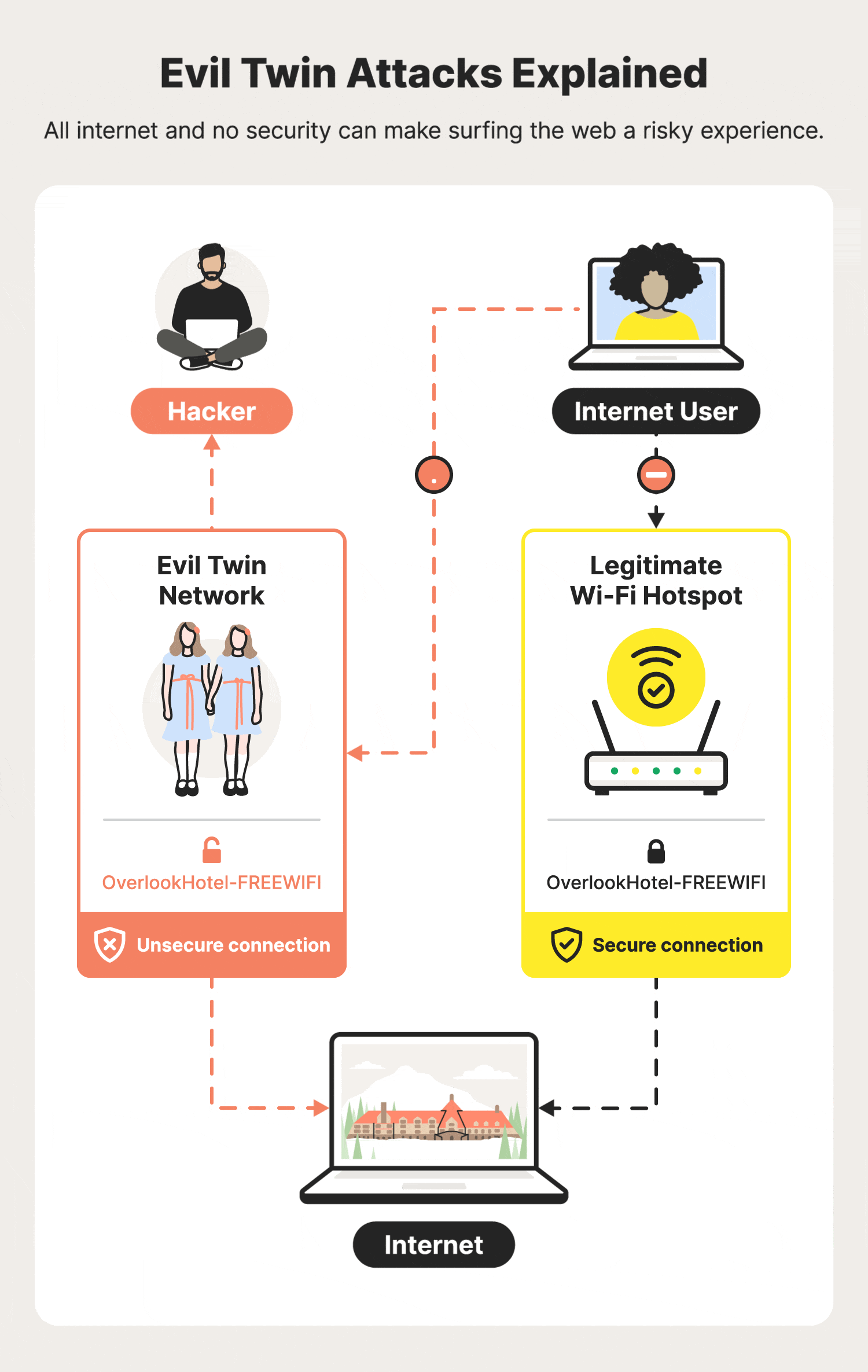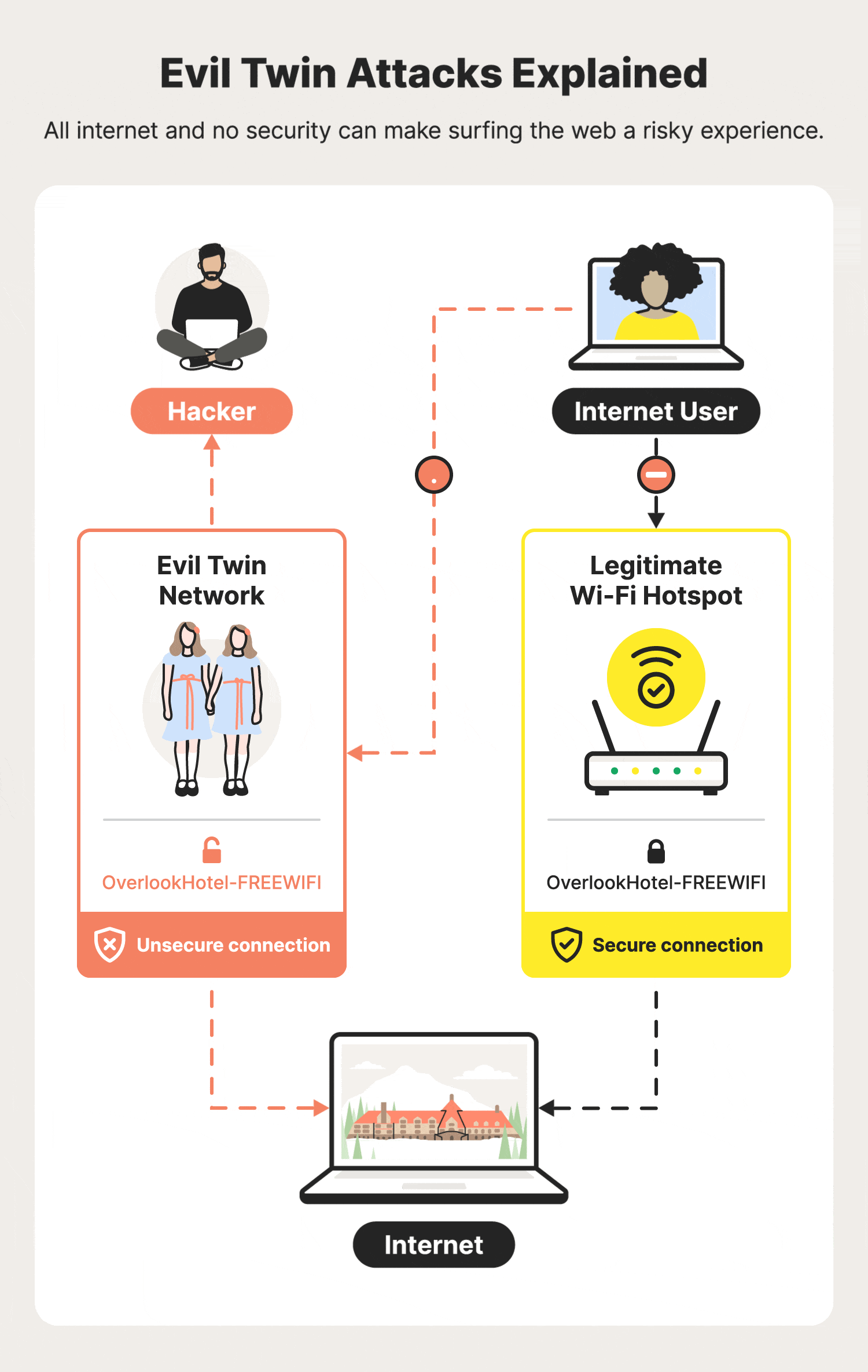
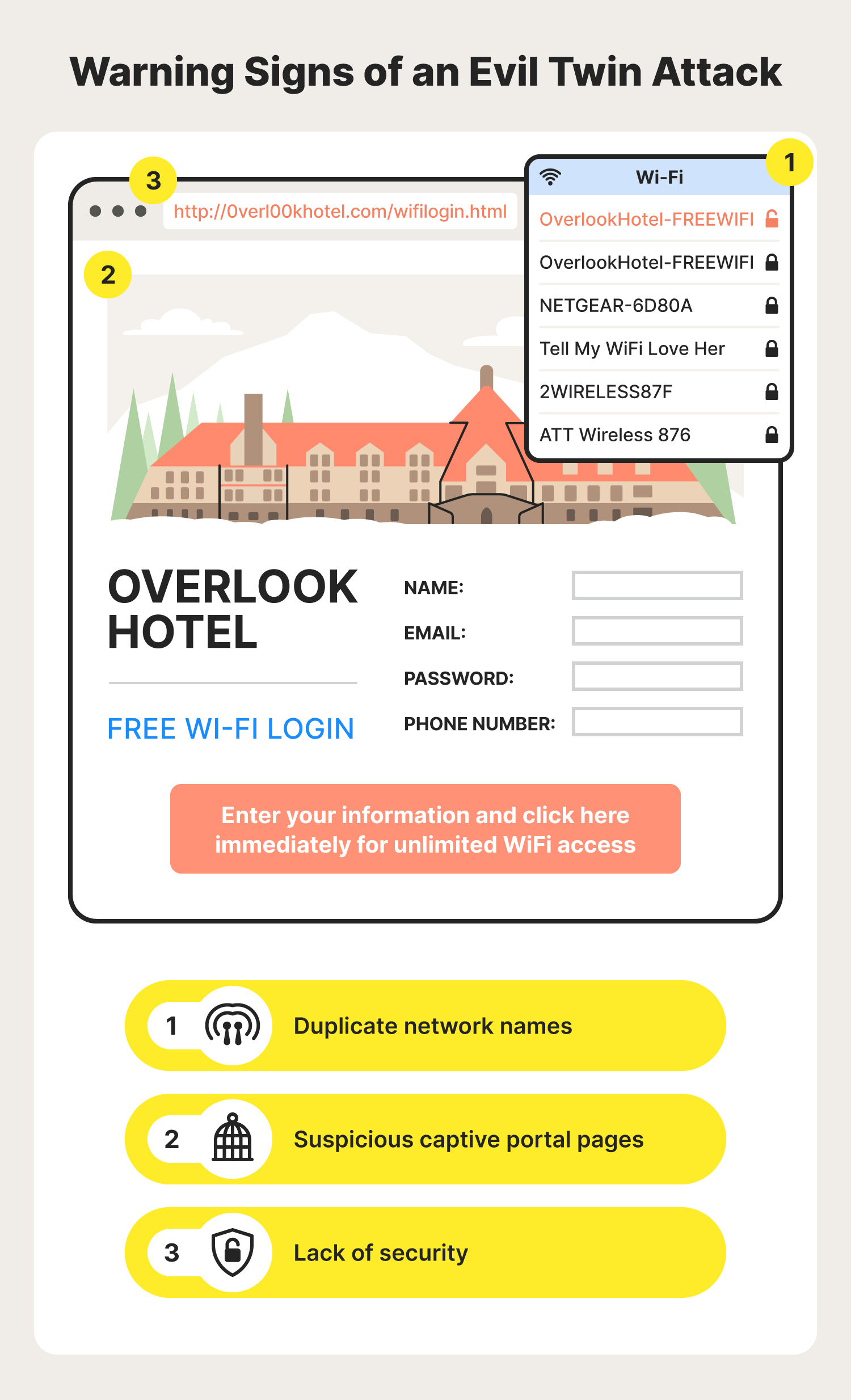
A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library

Gateway independent user-side wi-fi Evil Twin Attack detection using virtual wireless clients - ScienceDirect

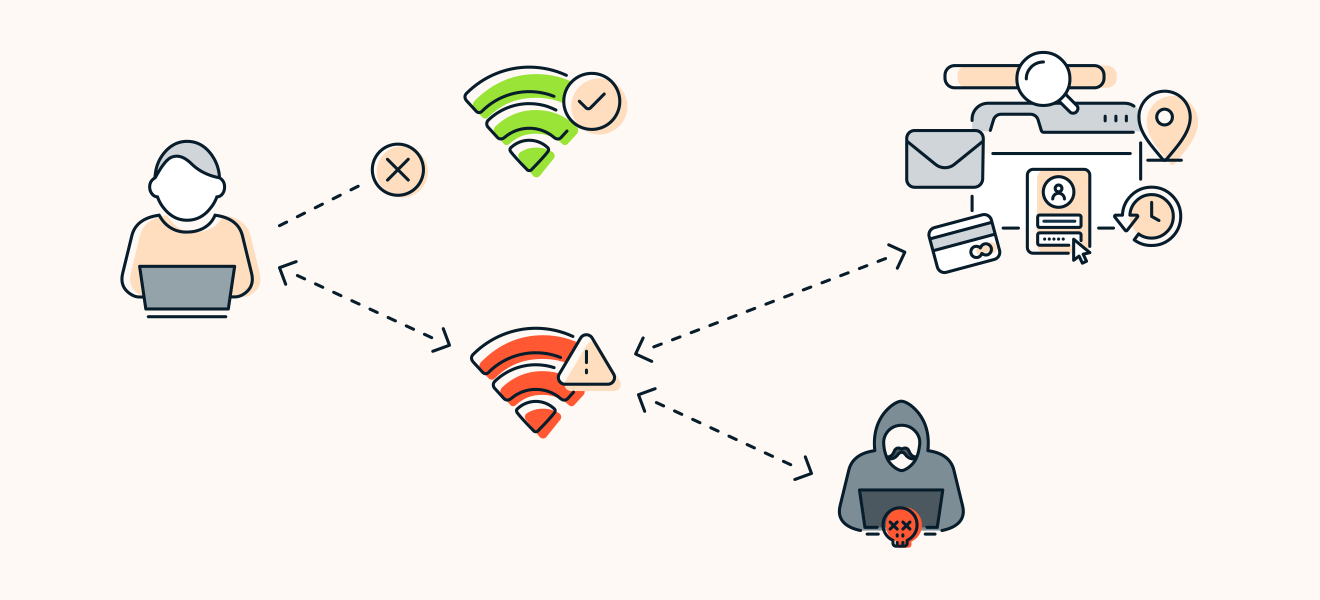
Day 2 of #CyberSecurity Awareness month: Evil Twin! ☠ #eviltwin | Lakshmi Chakravarthi posted on the topic | LinkedIn

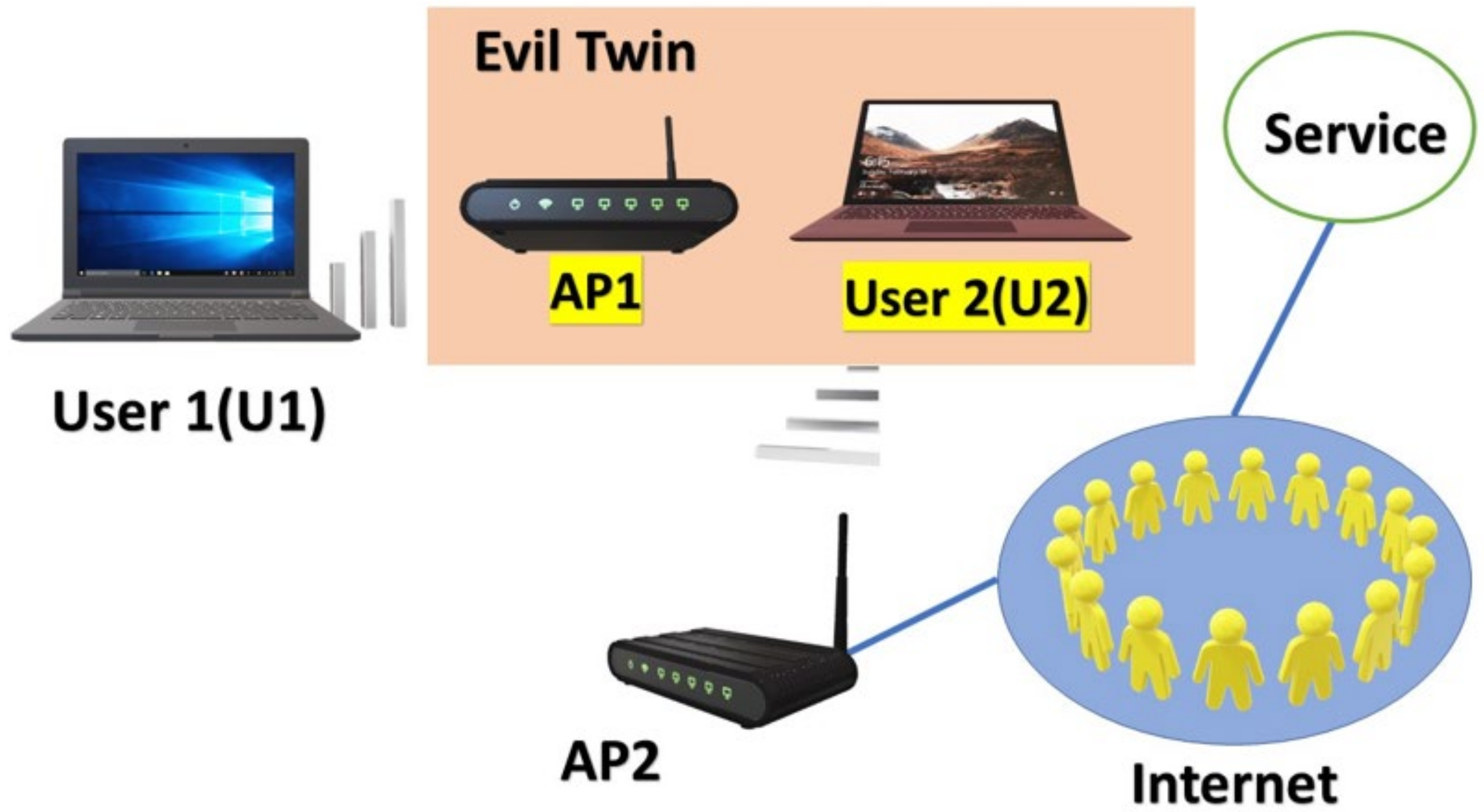
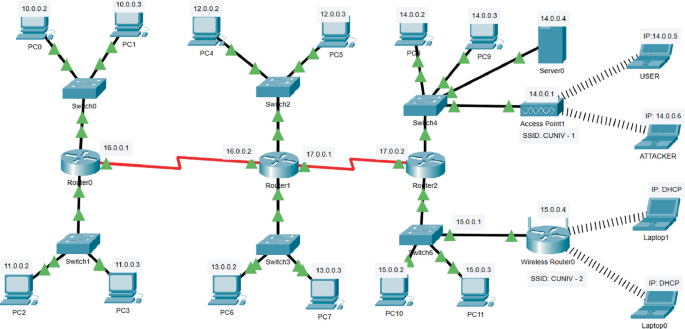
Case 4: Multiple genuine APs and multiple evil twin APs; a sub-set of... | Download Scientific Diagram

A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library
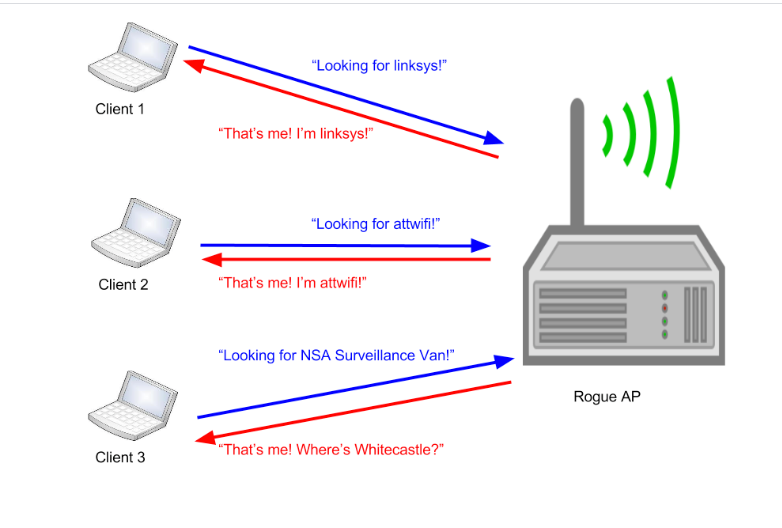
Modern Wireless Tradecraft Pt I — Basic Rogue AP Theory — Evil Twin and Karma Attacks | by Gabriel Ryan | Posts By SpecterOps Team Members

A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library